The CFO’s Role in Managing Cybersecurity Threats and Risks
Guest Contributor: Vijay Kumar. Vijay is the Founder & CEO of DigiFortex, an emerging Cyber Security company.
Introduction

At the World Economic Forum in 2022, Microsoft’s Satya Nadella said that Russia’s cyber onslaught on Ukraine started 1 year before its special military operation on February 24, 2022. While the Russian invasion had a combination of troops, tanks, aircraft, and cruise missiles, the first shots were in fact fired hours before when the calendar still said February 23 that involved a cyberweapon called “Foxblade” that was launched to cripple Ukraine’s digital signals and to distract the whole country before an actual military operation was formally launched. Within days, Ukraine immediately retaliated by hiring hundreds of global security experts/hackers to launch similar offensive cyber-operations on sensitive Russian entities, the aftereffects of which were globally felt. Security today is much beyond tanks, missiles, frigates, torpedoes, or fighter jets. Implicit earlier, cyber warfare is an offensive digital stratagem while cyber security - a defensive one. The Ukraine war teaches that National Security today must encompass safeguarding data integrity, availability, confidentiality, data privacy and data security.
When it comes to business, today increasing number of organizations are implementing various digital, data, analytics, and AI solutions for improved business performance. These trends have created tremendous business advantages, but they have also resulted in increased risks and threats in cybersecurity. According to IBM, the average cost of a data breach in 2023 was USD 4.45 million, up 15% over the last three years [1]. As cyberattacks have the power to disrupt, damage or destroy businesses, organizations are looking at implementing robust cybersecurity solutions. But what exactly is cybersecurity? In general, Cybersecurity refers to a wide range of technologies, processes, and practices to protect digital assets. To launch a cyber attack, cybercriminals use a variety of methods such as the ones listed below:
- Social engineering attacks use deception, coercion, and similar techniques to induce the target to do what the attacker wants.
- Phishing attacks use malicious messages with an embedded link or an attached file. If the user clicks on the link or opens the file, they may be taken to a webpage that steals sensitive information or install malware on their device.
- Botnets (a combination “robot” and “network”) is a malware that infects a digital asset to carry out commands under the remote control of the attacker.
- A zero-day exploit is a cyberattack vector that takes advantage of an unknown or unaddressed security flaw in digital assets. “Zero day” refers to the fact that the organization has zero days to fix the flaw given that malicious actors already have access to the compromised systems.
- Malware or malicious software is a program to steal, encrypt, and delete sensitive data, alter, or hijack core computing functions, and monitor end users’ computer activity.
To prevent this cyberattacks the CFO plays a significant role in every organization. But why is the CFO responsible for Cybersecurity which is an IT issue? The Chief Financial Officer (CFO) is typically not the individual directly responsible for cybersecurity within an organization, and the primary responsibility for cybersecurity typically falls under the Chief Information Security Officer (CISO) or Chief Information Officer (CIO). But many SMEs (small and medium enterprises) don’t have a CISO, let alone a CIO. In that case the CFO will be solely responsible and accountable for protecting the digital assets. Regardless, here are my 3 reasons on why the CFO needs to play a crucial role in cybersecurity efforts in the company.
- Cybersecurity is strongly tied to financial risk management. Given that CFOs are responsible for protecting the assets of the firm, managing the cyber threats and risk associated with the digital assets also come under the responsibility of the CFO.
- The CFO need to ensure that organization remains compliant with relevant regulations and standards as noncompliance to external regulations and internal control can result in hefty fines. For example, the #sox and #dataprivacy regulations require cybersecurity measures that limit ransomware attacks, phishing, data breaches, and more.
- The CFO is responsible for budgeting and resource allocation in the firm. As cybersecurity initiatives often require significant investments, the CFO’s involvement is crucial in ensuring that adequate funding is allocated for cybersecurity measures including disaster recovery, cyber insurance policies, training, and more.
Basically, cybersecurity is not IT risk. it is a business risk. A recent PwC survey found that 75% of CFOs are now involved in making high-level cyber security decisions. This is mainly because cybersecurity mistakes have major consequences. A report from Tessian found that almost one-third of businesses lost customers after an email was sent to the wrong person [2]. A cyber security incident can lead to a significant drop in stock prices, eroding shareholder trust and value. According to a 2021 study by Comparitech, companies that experienced data breaches saw their stock prices decline by an average of 7.27% in the days following the breach [3].
Implementing Cybersecurity Solutions
So how can CFOs or enterprises implement cybersecurity solutions to protect the digital assets from the growing cybersecurity threats? In this regard, cybersecurity solution can be implemented and managed in four phases as shown and explained below.
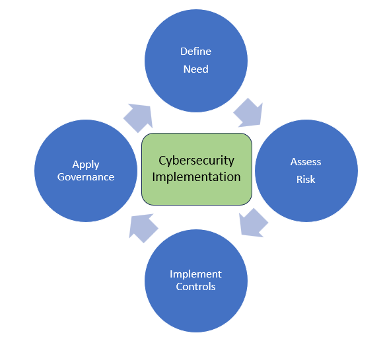
Phase 1: Define Need
Begin the cybersecurity journey by understanding and identifying the need and drivers. Is it regulations (such as CCPA or GDPR or HIPPA) or is it compliance to industry regulations (such as PCI DSS or SoX) or is to protect sensitive data or is it system availability or internal control requirements or is it anything else? Specially focus on why and why now?
Phase 2: Assess Risks
Once you have defined the need and got the context, support the reasons by evaluating the potential threat risks or vulnerabilities associated with the digital assets if a cybersecurity breach were to happen. Evaluating the cyber threats and risks by ranking and prioritizing the risks is important because not all risks have the same consequence/impact and likelihood. The Factor Analysis of Information Risk (FAIR) Model can be used to quantify cyber risk exposure. However, not all cyber risks can be eliminated or brought to the acceptable risk levels. Some risks will be present as residuals and can even come back in a different shape and form. These residual risks need to be constantly monitored by maintaining a risk register and keeping a close watch on the factors that impact them.
Phase 3: Implement Controls
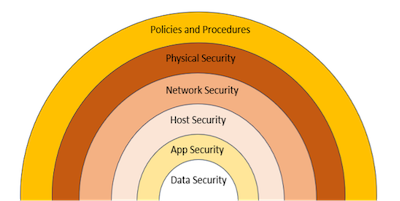
This step is the heart of implementation. It includes implementing cybersecurity controls to prevent, detect, and mitigate cyber threats and attacks. In this regard, defense-in-depth, is a layering security control approach where multiple layers of cybersecurity controls are implemented. Defense in depth was conceived from the National Security Agency (NSA) as a comprehensive approach to protect an organization’s digital assets. The thinking is that if one line of defense is compromised, additional layers exist as a backup to ensure that threats are stopped along the way. Basically, by layering and even duplicating security measures, the likelihood of a breach is minimized, and the digital infrastructure is hardened or protected. Image below shows the six “Defense in Depth” layers where the hardening measures need to be implemented including Perimeter Security, Logical Security, Digital Security, Mobile device Security, hybrid cloud security, threats from BYOD devices, Insider threats and many more that are looping and insidious in nature [4].
Phase 4: Apply Governance
Cybersecurity is not a one-time endeavour. It is an ongoing process that requires vigilance, regular or on-going updates, and a proactive approach to stay ahead of emerging threats. In this regard, below are some the governance practices an organization can follow.
- Provide cybersecurity training and awareness programs for all employees.
- Develop an incident response plan (IRP) that outlines the steps to take in the event of a security breach and the procedures for containing the incident, mitigating its impact, and restoring normal operations.
- Develop and frequently test a BCP/DR in case of a Ransomware incident. These days disasters could strike anyone anytime.
- A cyber insurance policy to pay for any financial losses they may incur in the event of a cyberattack or data breach.
- Assess and manage the security risks posed by third-party suppliers who have access to the systems and data.
- Constantly assess the state of redundant obsolete trivial (ROT) data and archive or purge them as per the records management policy of the company.
- Conduct regular audits like the ISO 27001:2022, HIPPA and SOC 2 Type II to ensure that the organization complies with the cybersecurity best practices.
- Frequently evaluate role-based authorisation access
- Implement MFA (multifactor authentication), DLP (Data Leakage Policy) (Zero Trust Policies.
- Conduct frequent proactive Vulnerability Assessment and Penetration Testing (VA/PT), Cloud Security Assessment to understand threats in your ecosystem, applications, network, hardware and mobile amongst others.
- Conduct table top exercises to limit the threats from Phishing.
- Implement 24/7 security monitoring through a SOC (Security Operation Center) as a defensive security strategy.
- Onboard a fractional CISO if not a full time to continuously manage, monitor and mitigate.
Conclusion
Implementing effective cybersecurity measures is particularly challenging today because of the increase size, scale, and complexity of the digital infrastructure. In addition, the hackers or attackers are becoming more innovative, global and at times state sponsored. But there is not called 100% secure cyber infrastructure. Implementing cybersecurity measures is a balance between protection and performance. If very strong cybersecurity measures are implemented, business performance will get adversely impacted. A 100% secure system might even be unusable. On the other hand, poor security measures might allow entities with malicious intentions to get inside the organizations and cause disruption to business. A successful cybersecurity solution has multiple layers of protection where the people, processes, and technology all complement one another to create an effective defense from cyber attacks.
Reference
- https://www.ibm.com/topics/cybersecurity#:~:text=For%20example%2C%20according%20to%20IBM’s,higher%2C%20at%20USD%205.13%20million.
- https://www.tessian.com/blog/new-research-psychology-of-human-error/
- https://www.forbes.com/sites/sergeiklebnikov/2019/11/06/companies-with-security-fails-dont-see-their-stocks-drop-as-much-according-to-report/?sh=30caf3f62e04
- https://www.cybernx.com/b-defense-in-depth-7-layers-to-secure-your-digital-data
Identify your path to CFO success by taking our CFO Readiness Assessmentᵀᴹ.
Become a Member today and get 30% off on-demand courses and tools!
For the most up to date and relevant accounting, finance, treasury and leadership headlines all in one place subscribe to The Balanced Digest.
Follow us on Linkedin!
